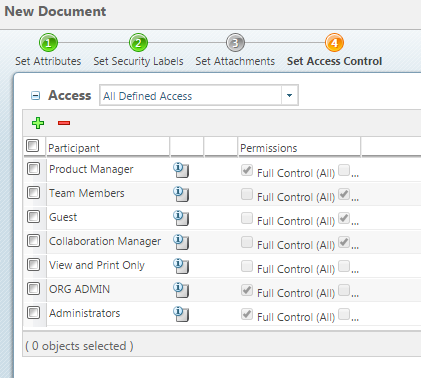
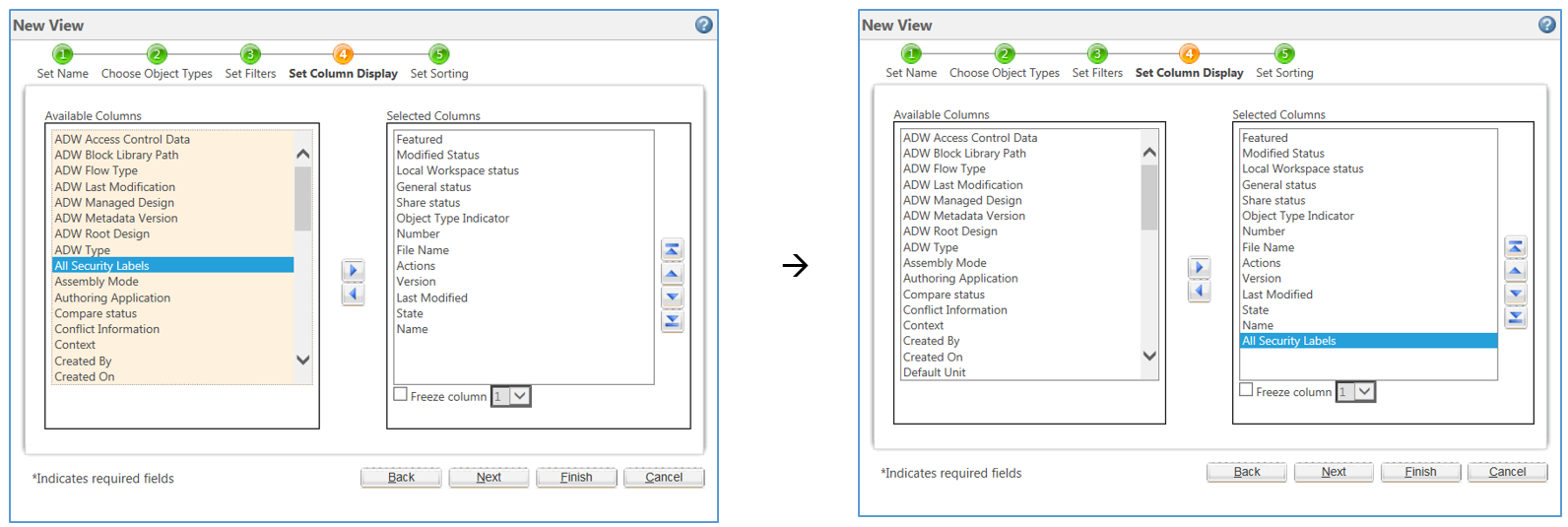
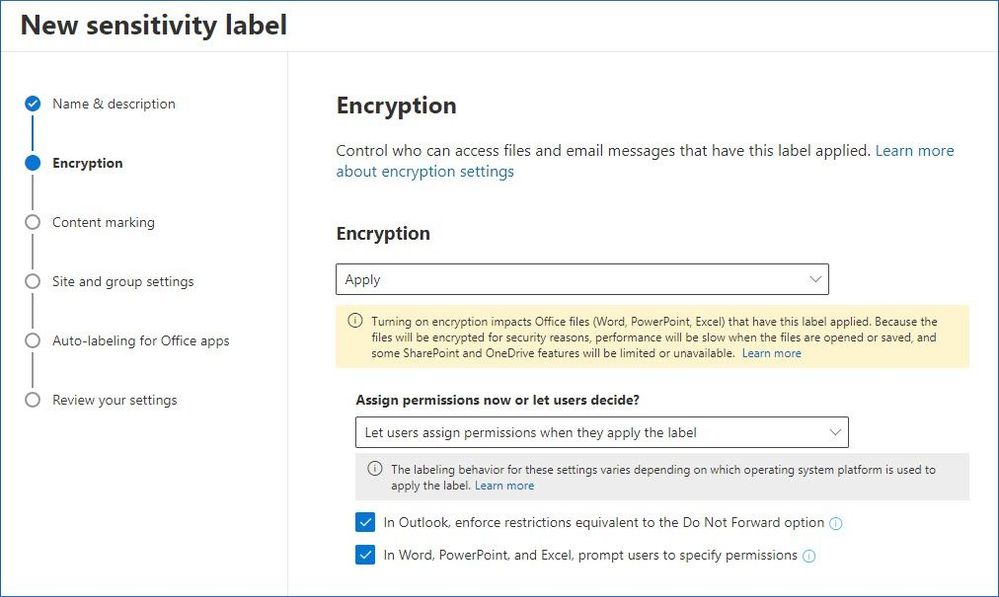
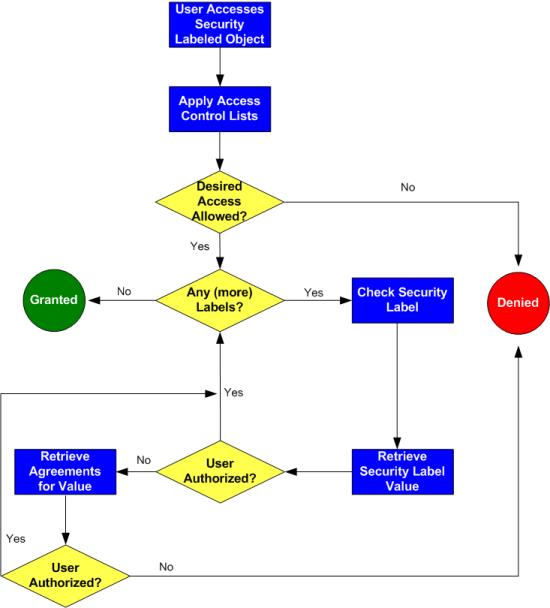
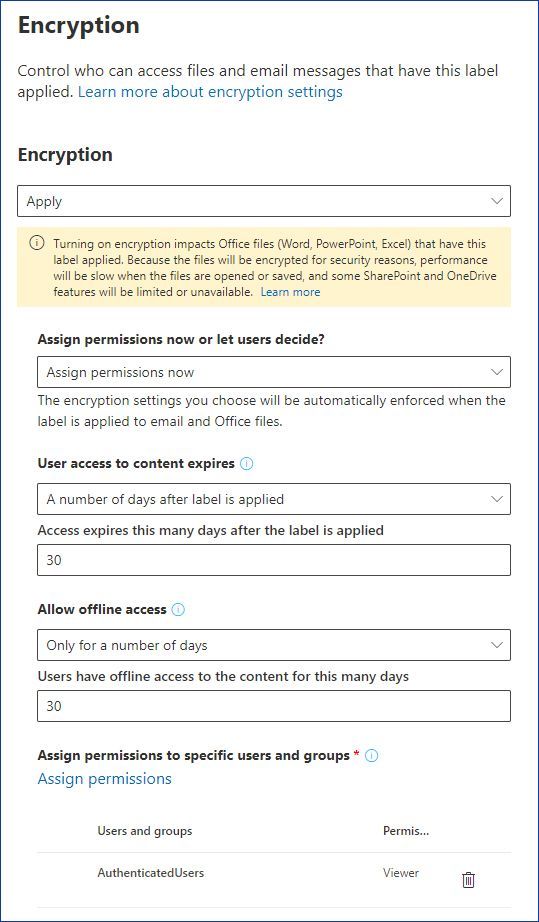
45 security labels access control
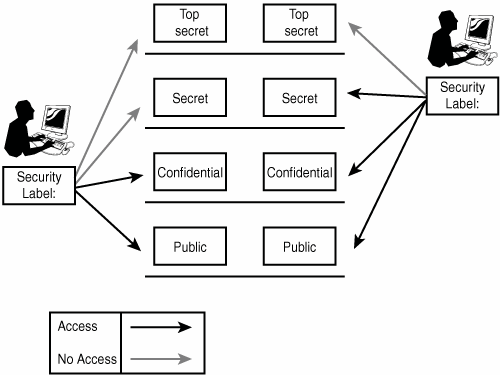
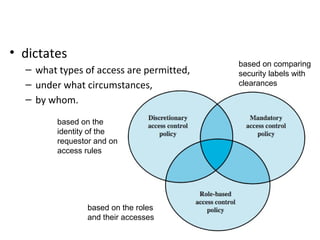
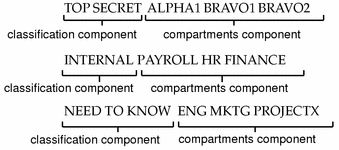
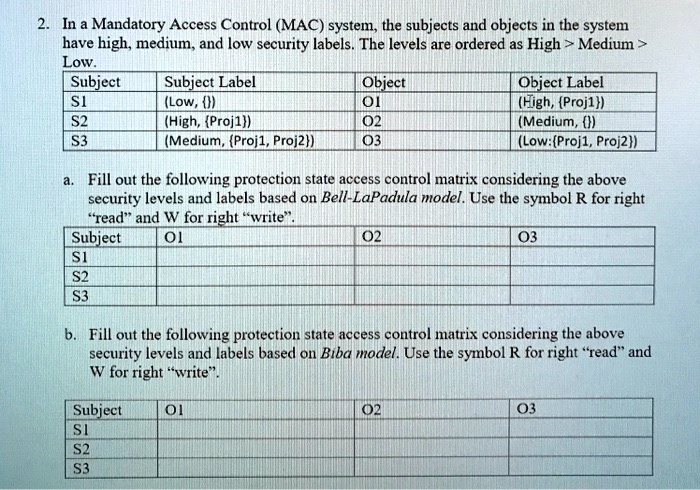
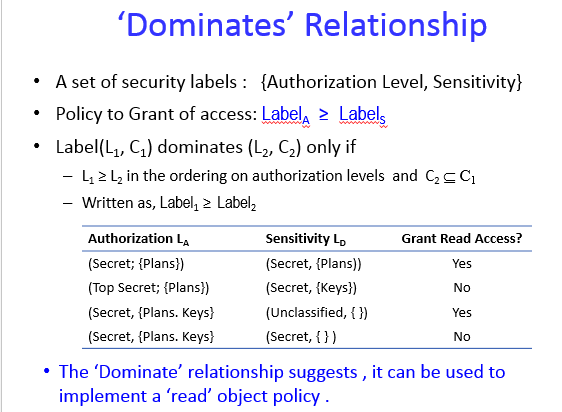
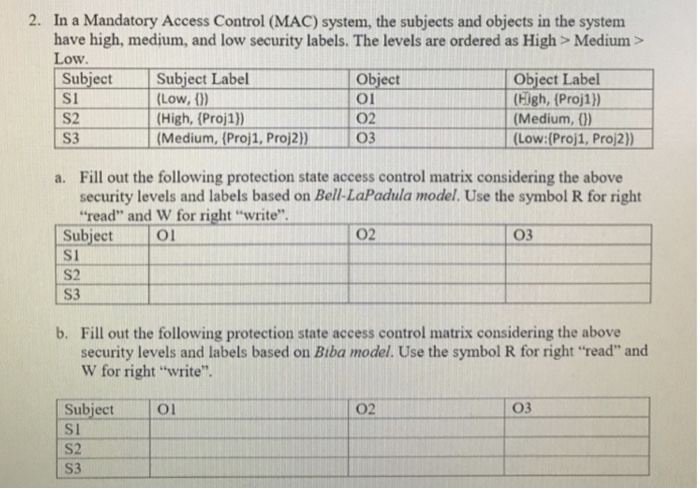
Bell–LaPadula model - Wikipedia The model is a formal state transition model of computer security policy that describes a set of access control rules which use security labels on objects and clearances for subjects. Security labels range from the most sensitive (e.g., "Top Secret"), down to the least sensitive (e.g., "Unclassified" or "Public"). Sign in to your account - admin.microsoft.com Email, phone, or Skype. No account? Create one! Can’t access your account?
Mandatory access control - Wikipedia Sun's Trusted Solaris uses a mandatory and system-enforced access control mechanism (MAC), where clearances and labels are used to enforce a security policy. However note that the capability to manage labels does not imply the kernel strength to operate in multilevel security mode [ citation needed ] .
Security labels access control
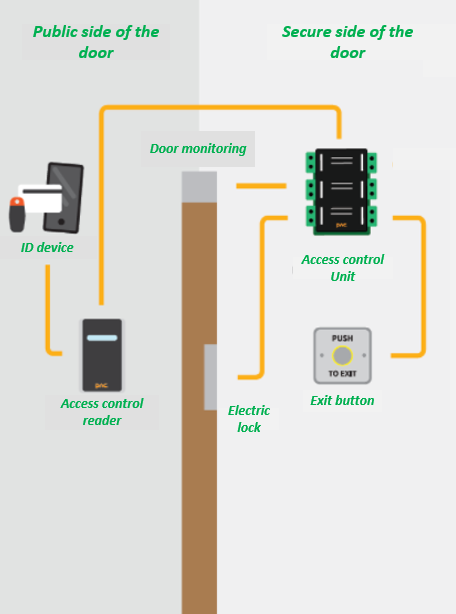
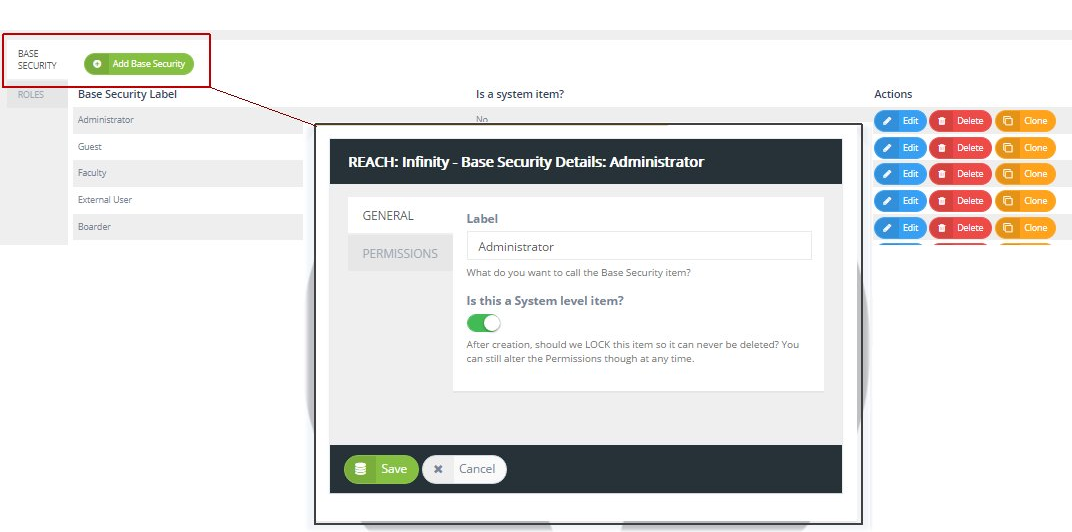
Access control for projects with IAM | Resource Manager ... Oct 12, 2022 · IAM lets you adopt the security principle of least privilege, so you grant only the necessary access to your resources. IAM lets you control who (users) has what access (roles) to which resources by setting IAM policies, which grant specific roles that contain certain permissions. Microsoft 365 Roadmap | Microsoft 365 Your Signature settings are stored in the cloud, so your experience is consistent when you access Outlook for Windows on any computer. This feature has been delayed and will only be available in Beta Channel. Feature ID: 60371; Added to Roadmap: 01/19/2020; Last Modified: 05/05/2022 Products - Red Hat Customer Portal Infrastructure and Management Red Hat Enterprise Linux. Red Hat Enterprise Linux (RHEL) is the world's leading open source operating system that provides an intelligent, stable, and security-focused foundation for modern, agile business operations.
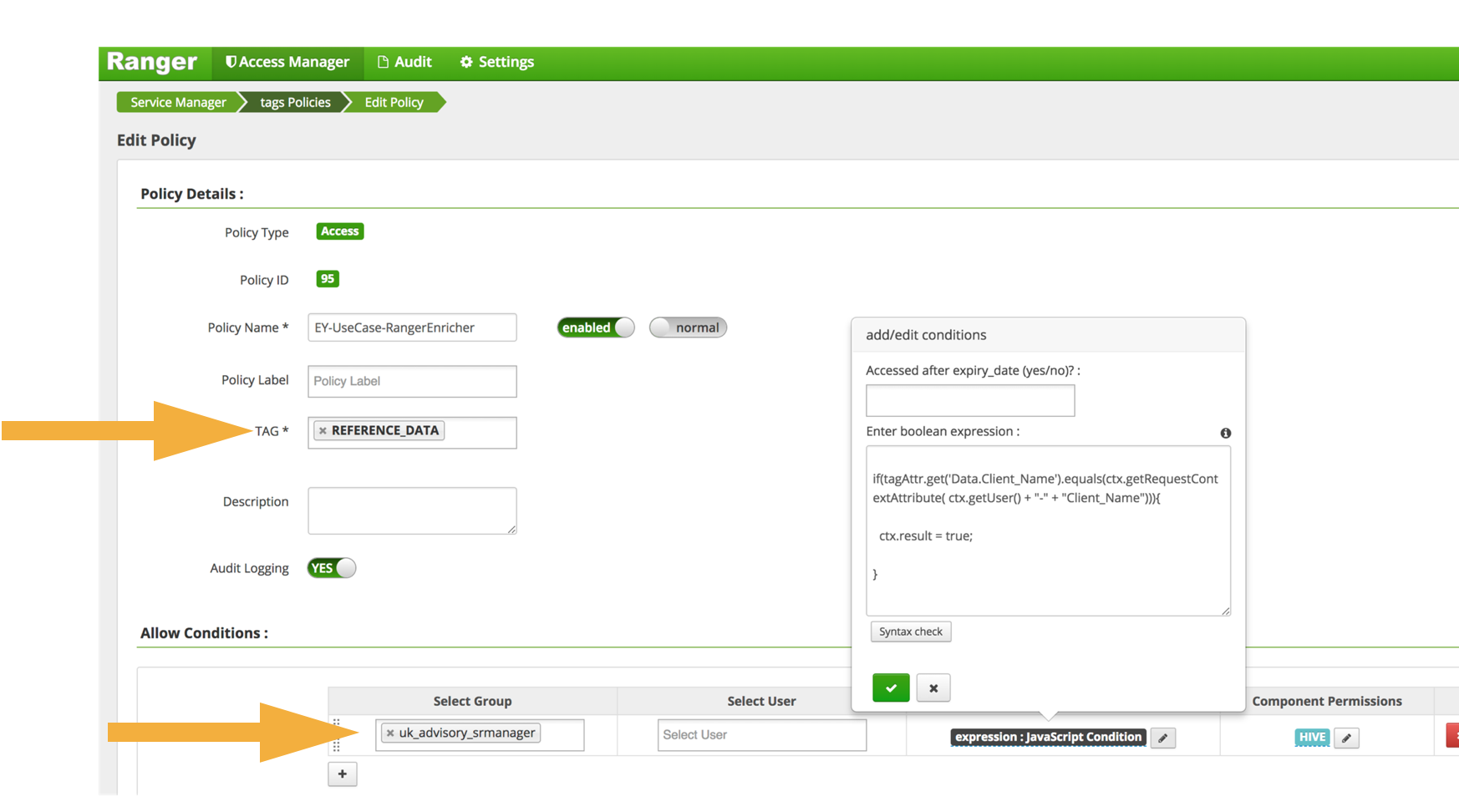
Security labels access control. Administrator privilege definitions - Google Workspace Admin Help Add security label to a group—Admins can define groups that control access to sensitive information and resources. For details see Updating a Google Group to a security group . If you create a custom role, you can check the box next to the privilege to allow using the API to perform all actions on that object. Products - Red Hat Customer Portal Infrastructure and Management Red Hat Enterprise Linux. Red Hat Enterprise Linux (RHEL) is the world's leading open source operating system that provides an intelligent, stable, and security-focused foundation for modern, agile business operations. Microsoft 365 Roadmap | Microsoft 365 Your Signature settings are stored in the cloud, so your experience is consistent when you access Outlook for Windows on any computer. This feature has been delayed and will only be available in Beta Channel. Feature ID: 60371; Added to Roadmap: 01/19/2020; Last Modified: 05/05/2022 Access control for projects with IAM | Resource Manager ... Oct 12, 2022 · IAM lets you adopt the security principle of least privilege, so you grant only the necessary access to your resources. IAM lets you control who (users) has what access (roles) to which resources by setting IAM policies, which grant specific roles that contain certain permissions.



























Post a Comment for "45 security labels access control"